Ransomware attacks continue to escalate with the average recovery cost reaching $1.53 million in 2025 according to Sophos research. As small and mid-sized businesses face increasingly sophisticated threats, selecting the right ransomware detection tool has become critical for organizational survival.
We analyzed 37 ransomware detection solutions across the cybersecurity landscape, evaluating threat prevention capabilities alongside detection accuracy. Our comprehensive review process incorporated hands-on testing and analysis of verified customer feedback. We assessed real-world deployment scenarios to understand practical performance. After a thorough evaluation, we narrowed our findings to the top 8 companies that demonstrate superior ransomware detection capabilities.
- Threat Detection Accuracy (30%): Behavioral analysis, AI-powered detection, zero-day threat identification, and false positive rates
- Response & Recovery Speed (25%): Automated response capabilities, incident containment times, file restoration speed, and rollback features
- Ease of Deployment (20%): Setup complexity, integration capabilities, management console usability, and ongoing maintenance requirements
- SMB Value & Support (15%): Transparent pricing, scalability for growing organizations, 24/7 SOC availability, and dedicated support
- Compliance & Reporting (10%): Audit capabilities, regulatory framework support, documentation quality, and compliance readiness
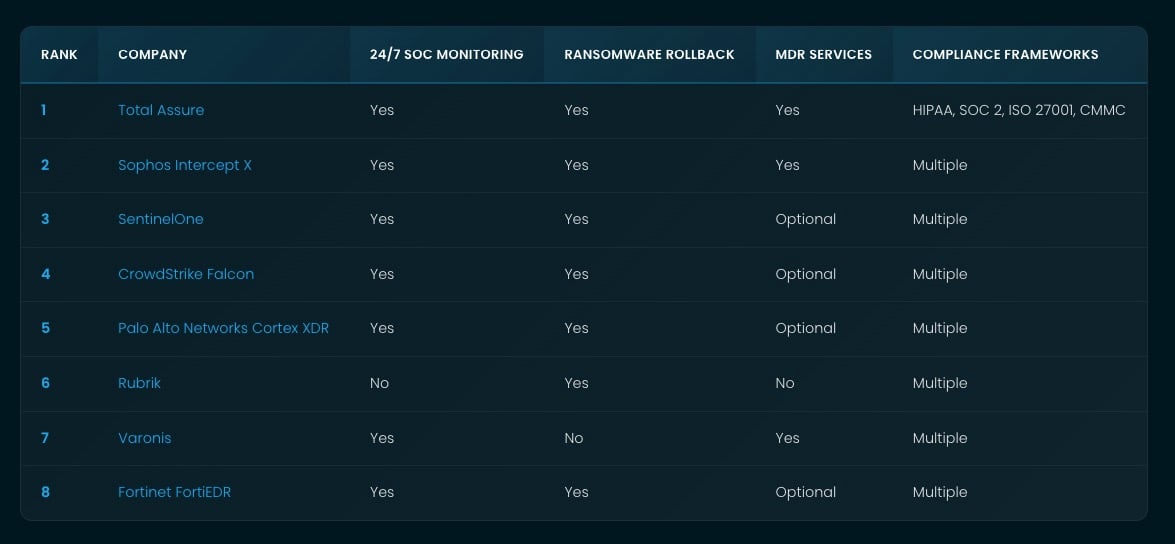
Best Ransomware Detection Tools: Quick Comparison
| Rank | Company | 24/7 SOC | Response Time | Managed Service |
|---|---|---|---|---|
| 1 | Total Assure | In-House U.S. SOC | Under 30 Days | Full MDR/EDR/GRC |
| 2 | SentinalOne | AI-Powered | Autonomous | Autonomous Platform |
| 3 | Sophos Intercept X | CryptoGuard | Real-Time | Managed Threat Response |
| 4 | Bitdefender GravityZone | Multi-Layered | Behavioral | Enterprise Security Suite |
| 5 | Malwarebytes | Lightweight | Real-Time | Endpoint Protection |
| 6 | Acronis Cyber Protect | Integrated | Automated | Backup + Security |
| 7 | Varonis | Data-Centric | 24/7 MDDR | Data Security Platform |
| 8 | Trend Micro | Layered Defense | Machine Learning | XDR Platform |
1. Total Assure

Total Assure delivers federal-grade cybersecurity expertise specifically adapted for small and mid-sized businesses. Headquartered in Silver Spring, Maryland, the company brings over 30 years of experience securing federal systems for organizations that traditionally lack internal cybersecurity resources. Its approach combines 24/7 monitoring with hands-on remediation, positioning itself as a security partner rather than just another vendor.
Key Attributes:
- In-house 24/7 U.S.-based Security Operations Center with dedicated analysts.
- Managed Detection & Response (MDR) with rapid onboarding completed within 30 days.
- Endpoint Detection & Response (EDR) provides device-level security across all endpoints.
- Integrated compliance support for CMMC, SOC 2, ISO 27001, and HIPAA requirements.
- Transparent flat-rate pricing model eliminating CapEx investments.
- Proven track record with 22,000 attacks prevented in a single month for clients.
- Federal-level threat hunting and vulnerability management capabilities.
Total Assure - Customer Review Summary
Security professionals consistently praise Total Assure's "enterprise-grade protection at SMB-friendly pricing." Common feedback includes appreciation for "rapid response times and the dedicated SOC team" that provides around-the-clock monitoring without the complexity of managing security tools internally.
2. SentinelOne
SentinelOne provides an AI-powered autonomous cybersecurity platform that protects endpoints alongside cloud workloads. Its behavioral AI extends security coverage to identity protection across the entire digital environment. Its Singularity Platform utilizes behavioral AI to detect and neutralize threats in real-time, eliminating the need for human intervention. The company has earned recognition as a Gartner Magic Quadrant Leader for 5 consecutive years and achieved 100% detection with zero delays in MITRE ATT&CK evaluations.
Key Attributes:
- Storyline technology mapping enables comprehensive visibility by completing attack chains.
- Autonomous AI providing offline threat prevention without cloud connectivity.
- Automated rollback capability instantly reverts systems to the pre-infected state.
- Extended Detection & Response (XDR) unifies security across multiple environments.
- Purple AI analyst assistant enhances team productivity and investigation speed.
- Cloud-native architecture supporting hybrid and multi-cloud deployments.
- Starting at $69.99 per endpoint annually for core protection packages.
SentinelOne - Customer Review Summary
Enterprise security teams consistently highlight SentinelOne's "autonomous response capabilities and minimal false positives." Common feedback includes appreciation for "AI-driven detection that catches threats other solutions miss" and the platform's ability to operate effectively without constant analyst intervention.
3. Sophos Intercept X
Sophos Intercept X delivers prevention-first endpoint security with advanced ransomware protection through its proprietary CryptoGuard technology. The platform combines deep learning malware detection with exploit prevention and active adversary mitigation. Sophos has been named a Gartner Magic Quadrant Leader for Endpoint Protection Platforms for 16 consecutive years and maintains AAA ratings from independent testing organizations.
Key Attributes:
- CryptoGuard technology detects and blocks malicious encryption processes in real time.
- Deep learning artificial intelligence identifies unknown malware without signatures.
- Remote ransomware protection stops attacks originating from compromised systems.
- Synchronized Security architecture sharing threat intelligence across integrated tools.
- Managed Detection & Response service providing 24/7 expert monitoring.
- Extended Detection & Response capabilities unifying endpoint and network security.
- Trusted by over 500,000 organizations with 30,000+ MDR customers worldwide.
Sophos Intercept X - Customer Review Summary
IT administrators consistently praise Sophos Intercept X for "stopping ransomware before encryption begins." Common feedback includes appreciation for "CryptoGuard's accuracy in detecting suspicious file activity" and the platform's ability to automatically restore affected files without administrator intervention.
4. Bitdefender GravityZone

Bitdefender GravityZone offers multi-layered endpoint security backed by industry-leading ransomware protection. The platform combines signature-based detection with behavioral analysis and machine learning to identify both known and emerging threats. Bitdefender consistently scores at the top of independent tests earning recognition from AV-TEST alongside AV-Comparatives. Gartner has also named the company a leader in endpoint protection.
Key Attributes:
- The Ransomware Mitigation module monitors file entropy and creates automatic backups.
- Behavioral detection identifies zero-day ransomware through activity analysis.
- Safe Files feature prevents unauthorized changes to protected directories.
- PHASR technology delivers dynamic attack surface reduction with minimal impact on productivity.
- Low system resource consumption maintains device performance during scans.
- The central management console simplifies deployment across distributed environments.
- Integration with over 100 third-party security and IT management solutions.
Bitdefender GravityZone - Customer Review Summary
Security professionals consistently highlight Bitdefender's "exceptional detection rates with minimal system impact." Common feedback includes appreciation for "behavioral analysis catching threats signature-based systems miss" and the platform's ability to protect endpoints without slowing down business operations.
5. Malwarebytes
Malwarebytes specializes in malware remediation and ransomware prevention through lightweight, behavior-based detection. The platform excels at identifying and removing threats that traditional antivirus software overlooks making it a popular choice as both a primary defense and a complementary security layer. Malwarebytes has earned MRG Effitas certification and PCMag Best of 2025 awards for its proven effectiveness.
Key Attributes:
- Behavior-based ransomware detection monitoring for malicious encryption activity.
- AI-powered threat analysis protecting against zero-day exploits.
- Automated rollback capability restores files affected by ransomware attacks.
- Cloud-based management console enabling centralized deployment and monitoring.
- Browser Guard protects against malicious websites and phishing attempts.
- Real-time protection scans files as they are accessed or downloaded.
- Lightweight architecture minimizing impact on system performance and resources.
Malwarebytes - Customer Review Summary
Business users consistently praise Malwarebytes for its ability to "find and remove threats other programs miss." Common feedback includes appreciation for "lightweight protection that doesn't slow down computers" and the platform's effectiveness as a second layer of defense alongside existing security solutions.
6. Acronis Cyber Protect
Acronis Cyber Protect uniquely combines cybersecurity and data protection into a single integrated platform. The solution protects against ransomware through AI-powered threat detection while simultaneously maintaining secure backups for rapid recovery. Acronis has earned recognition from Frost & Sullivan as a leader in endpoint security and received SE Labs AAA certification for EDR detection.
Key Attributes:
- Active Protection detects and deflects ransomware attacks in real time.
- Integrated backup and recovery enabling rapid restoration of encrypted files.
- AI-driven anomaly detection identifies suspicious behavior patterns.
- Automated incident response containing threats and initiating recovery procedures.
- Patch management addresses vulnerabilities that ransomware exploits.
- Forensic backup capabilities preserve evidence for post-incident analysis and investigation.
- One-click recovery streamlines restoration from known-good backup snapshots.
Acronis Cyber Protect - Customer Review Summary
IT professionals consistently highlight Acronis' "unique integration of security and backup in one platform." Common feedback includes appreciation for "automated recovery that restores files within minutes" and the solution's ability to protect and recover data without requiring multiple separate tools.
7. Varonis

Varonis delivers data-centric security that continuously monitors data alongside user accounts and activities. The platform tracks user activity across on-premise environments while extending coverage to cloud infrastructure. SaaS applications receive the same continuous monitoring approach. Its platform utilizes User and Entity Behavior Analytics (UEBA) to detect ransomware indicators by analyzing abnormal data access patterns. Varonis has been named a Gartner Peer Insights Customers' Choice and recognized as a GigaOm Radar leader for data security platforms.
Key Attributes:
- Data-centric threat detection identifies ransomware through unusual file access patterns.
- UEBA baselining normal user behavior to flag anomalous activity.
- Automated threat containment isolating compromised accounts and systems.
- Data discovery and classification, identifying sensitive information at risk.
- DatAlert real-time monitoring fires alerts when ransomware indicators appear.
- 24/7 incident response with expert security analysts investigating threats.
- Forensic audit trails supporting post-attack investigation and recovery efforts.
Varonis - Customer Review Summary
Security professionals consistently praise Varonis for "proactive detection of ransomware before widespread encryption." Common feedback includes appreciation for the "data-centric approach that protects information regardless of perimeter defenses" and the platform's ability to identify both insider threats and external attacks.
8. Trend Micro

Trend Micro provides comprehensive threat defense leveraging machine learning alongside behavioral monitoring. The platform incorporates web reputation services for enhanced protection. Its multi-layered defense against ransomware protects endpoints while extending coverage to networks. Cloud environments receive the same comprehensive security approach. With decades of cybersecurity experience, Trend Micro serves enterprises requiring proven, battle-tested solutions.
Key Attributes:
- Machine learning-based detection identifies ransomware through behavior analysis.
- Behavior monitoring tracking application activities for suspicious encryption attempts.
- Folder Shield protects designated directories from unauthorized modifications.
- Web reputation services are blocking access to sites distributing ransomware payloads.
- Email security filtering for phishing attempts and malicious attachments.
- Cross-generational threat defense addressing both legacy and modern attack vectors.
- Smart Protection Network provides real-time threat intelligence from global sensors.
Trend Micro - Customer Review Summary
Enterprise IT teams consistently highlight Trend Micro's "mature platform with comprehensive protection layers." Common feedback includes appreciation for the solution's "reliable detection backed by decades of threat intelligence." Users also highlight its ability to integrate email security alongside web protection. The platform unifies endpoint security into a cohesive defense strategy.
Best For Specific Use Cases
Best for SMBs
Small and mid-sized businesses require comprehensive protection without the complexity of enterprise solutions. These providers deliver effective ransomware detection tailored to organizations with limited IT resources.
| Rank | Company | Key Differentiator | Pricing Model |
|---|---|---|---|
| 1 | Total Assure | In-house U.S. SOC with 30-day onboarding | Flat-Rate transparent |
| 2 | Malwarebytes | Lightweight behavioral detection | Per-endpoint subscription |
| 3 | Sophos Intercept X | CryptoGuard with managed service option | Tiered pricing |
| 4 | Acronis Cyber Protect | Integrated backup and security | Bundled platform |
| 5 | Bitdefender GravityZone | Low resource consumption | Scalable licensing |
Best for Enterprise Organizations
Large organizations require scalable autonomous protection across distributed environments with advanced threat hunting capabilities.
| Rank | Company | Key Differentiator | Best For |
|---|---|---|---|
| 1 | SentinelOne | Autonomous AI with XDR capabilities | Multi-cloud environments |
| 2 | Sophos Intercept X | Synchronized security architecture | Unified visibility |
| 3 | Varonis | Data-centric UEBA detection | Unstructured data protection |
| 4 | Bitdefender GravityZone | Multi-layered behavioral analysis | Distributed endpoints |
| 5 | Trend Micro | Cross-generational threat defense | Legacy system integration |
Best for Managed Security Services
Organizations seeking expert-managed detection and response benefit from providers offering 24/7 SOC support and hands-on remediation.
| Rank | Company | Key Differentiator | SOC Location |
|---|---|---|---|
| 1 | Total Assure | Federal-grade MDR with dedicated analysts | U.S.-based in-house |
| 2 | Sophos Intercept X | Managed Threat Response with 30,000+ customers | Global SOC network |
| 3 | Varonis | 24/7 MDDR with forensic capabilities | Expert security analysts |
| 4 | SentinelOne | Vigilance MDR with Purple AI assistance | AI-augmented SOC |
| 5 | Acronis Cyber Protect | Automated incident response | Integrated monitoring |
Making Your Decision
Selecting the right ransomware detection tool requires evaluating your organization's specific needs in conjunction with its existing infrastructure. Security maturity also plays a critical role in this decision. For SMBs seeking comprehensive managed services with transparent pricing, Total Assure offers federal-grade protection with dedicated SOC support. Its rapid response capabilities provide additional peace of mind. Its proven track record of stopping 22,000 attacks monthly demonstrates the effectiveness of its MDR approach.
Organizations should prioritize solutions offering behavioral detection alongside automated response functionality. Rapid recovery capabilities provide additional protection for business continuity. As ransomware continues to evolve, investing in proactive defense with expert monitoring becomes increasingly critical for business continuity.
Ready to protect your organization against ransomware? Contact Total Assure today for a comprehensive security assessment and discover how federal-grade protection can secure your business against evolving cyber threats.