
What SMBs Need to Know About Endpoint Detection and Response (EDR)
Every device your business uses is a potential entry point for cyber threats. Endpoint Detection and Response (EDR) helps SMBs monitor, detect, and respond to these threats.
Total Assure's MES wraps multiple layers of advanced, AI-powered security around your existing email platform to protect your business from the full spectrum of email-based threats. We don't just block spam; we neutralize targeted phishing and malware before they ever reach an inbox. The key benefits are profound: protect your people from dangerous attacks, safeguard your data and finances, and ensure the integrity of your most critical communication channel. Total Assure's MES service provides:
Our Managed Email Security service functions as an intelligent, comprehensive filtration system that inspects all your inbound and outbound email, all without changing how your employees send and receive messages. The process is seamless to your users and provides immediate protection.
Our methodology is a continuous, four-stage cycle:
The process begins with a simple, behind-the-scenes change to your domain's MX records. This directs all your inbound email to our gateway for inspection before it reaches your mail server.
Each message passes through a multi-layered gauntlet of security checks. This includes Spam and Virus Filtering, which blocks bulk junk mail and known malware.
We use AI and machine learning to analyze emails for signs of targeted phishing, impersonation, and brand forgery characteristic of Business Email Compromise (BEC) attacks.
Any attachments are scanned and opened in a secure, isolated "sandbox" environment to see how they behave. If they attempt to do anything malicious, the email is quarantined.
We also scan all outbound email to prevent your own accounts, if compromised, from being used to attack your customers and partners, protecting your brand's reputation.
Clean, verified emails are delivered instantly to the user's inbox, while malicious ones are held in a secure quarantine that users and administrators can review.
Together with our partner, Avanan, we employ a cloud-based email security solution. With continuous monitoring, customized filters, and ongoing threat intelligence gathering, Total Assure's email security solution is what your business needs to stay in the game.
We utilize a best-in-class, cloud-native email security platform, recognized by analysts for its high efficacy and low false-positive rate. The technology is API-driven for deep integration with Microsoft 365 and Google Workspace, allowing for enhanced internal email protection and simple administration. Because the entire service is cloud-based, there is no hardware to install and no software to maintain on your end.
Our implementation timeline is designed for rapid protection with zero downtime:
Our MES service delivers a robust set of features that provide comprehensive protection and translate into significant business value and risk reduction.
The return on investment (ROI) for Managed Email Security is exceptionally high. By preventing a single BEC incident or ransomware attack, the service pays for itself many times over. The ROI is measured in avoided financial loss, preserved brand reputation, maintained regulatory compliance, and increased employee productivity due to less time spent dealing with malicious emails.
Yes, they provide good baseline security. However, they are the biggest targets, and cybercriminals design their attacks specifically to bypass these native defenses. Our service adds multiple, more advanced layers of specialized security to catch the threats that the default protection misses.
Not at all. The service is virtually invisible to end-users. They continue to use their email client (like Outlook or Gmail) as they always have. The only change they might notice is a dramatic reduction in spam and malicious emails in their inbox.
A false positive is when a legitimate email is incorrectly flagged as malicious. While our platform has an extremely low false-positive rate, our team continuously tunes the system to your specific needs. Legitimate emails are held in a secure quarantine where users can review and release them if needed.
Absolutely. While we provide a best-practice security posture out of the box, the policies are fully customizable. We can adjust the aggressiveness of the filtering for different users or groups (e.g., more stringent policies for the finance department).
BEC is a sophisticated attack where a scammer impersonates a high-level executive (like the CEO) or a trusted vendor to trick an employee into making an unauthorized wire transfer or sending sensitive information. Our AI-powered impersonation detection is specifically designed to stop these attacks.
Email is the entry point for many attacks, so pairing MES with our other services creates a robust, layered defense.
We can bundle these services to create a comprehensive security strategy that protects your entire organization.
Learn more about email security, phishing protection, and securing your communications.

Every device your business uses is a potential entry point for cyber threats. Endpoint Detection and Response (EDR) helps SMBs monitor, detect, and respond to these threats.

One of the best methods to protect your business from cyber attacks is by educating your employees about cybersecurity threats.
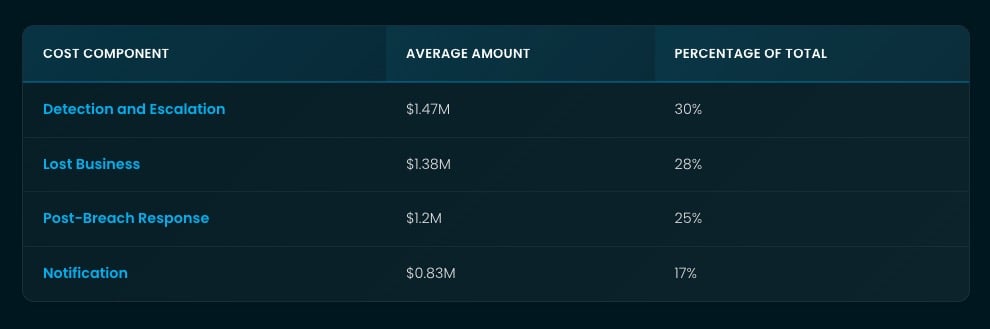
Average phishing attack costs for 2025 including direct losses, recovery expenses, downtime impact, and prevention strategies
Ready to stop email threats before they reach your inbox and threaten your business?
Contact Us