
What SMBs Need to Know About Endpoint Detection and Response (EDR)
Every device your business uses is a potential entry point for cyber threats. Endpoint Detection and Response (EDR) helps SMBs monitor, detect, and respond to these threats.
Your endpoints, the laptops, servers, and workstations your team uses every day, are the frontline of your business and the primary target for cyberattacks. We consistently identify and react to cyber threats affecting your organization's computing devices, whether they are residing within your network or not. Total Assure's EDR service provides:
Our EDR service is designed to provide comprehensive protection through a clear, continuous process, integrating powerful technology with your infrastructure seamlessly and efficiently.
Our methodology is a continuous, four-stage cycle:
A single, lightweight software agent is deployed to each of your endpoints. This agent continuously records relevant system activities, such as process creation, registry modifications, network connections, and user logins, and sends this telemetry to a centralized cloud platform for analysis. This creates a detailed, searchable history of every action taken on the device.
The platform uses machine learning, artificial intelligence, and behavioral analytics to sift through the collected data. It compares activities against known threat intelligence and, more importantly, identifies anomalous behaviors that indicate a potential attack, even from previously unknown malware.
When a threat is identified, the EDR platform provides our security analysts with powerful tools to understand the full story of an attack. We can visualize the entire attack chain, from the initial entry point to every subsequent action the attacker took. This "who, what, when, and where" is critical for a thorough response.
EDR allows for powerful remote actions to neutralize threats in seconds. This can range from automatically killing a malicious process and quarantining malware to isolating an infected endpoint from the network to prevent the threat from spreading.
Federal pedigree, SMB focused: our solution starts by leveraging top-tier EDR technologies with our partner, SentinelOne, combining traditional anti-malware with AI-driven behavioral analysis for more advanced threat detection. We then bring in our expert analysts who use the rich contextual and telemetry data from SentinelOne to identify and neutralize threats before they can harm your business.
We leverage a market-leading EDR platform, recognized by industry analysts like Gartner for its advanced capabilities. The technology consists of the lightweight endpoint agent and a cloud-native management console, ensuring minimal impact on device performance and infinite scalability.
Our implementation process is designed for speed and simplicity:
Our EDR service delivers a suite of powerful features that translate directly into enhanced security, reduced risk, and a stronger overall business posture.
The return on investment (ROI) for EDR is centered on breach prevention and operational efficiency. By stopping a single major ransomware incident, the service pays for itself many times over. Furthermore, it drastically reduces the time and resources your IT team would otherwise spend manually investigating and cleaning infected machines.
Traditional antivirus identifies malware based on known file signatures; it can only stop threats it has seen before. EDR focuses on behavior. It looks for the malicious actions an attacker takes, allowing it to detect and stop new, unknown, and fileless threats that traditional AV is blind to.
No. The endpoint agent is incredibly lightweight and optimized for minimal performance impact. It consumes very few CPU and memory resources, so your employees won't notice it's there.
Not anymore. While it originated in the enterprise space, our EDR service is priced and scaled to be accessible and affordable for small and medium-sized businesses. We believe every business deserves enterprise-grade protection.
No, that's the benefit of our service. Total Assure manages the platform, tunes the policies, investigates the alerts, and recommends response actions. We handle the security operations so you can focus on your business.
We can often work with your existing investment. Our team has expertise across multiple EDR platforms and can provide our monitoring and response services (MDR) by integrating with your current technology.
Endpoint security is a critical piece of the puzzle, but its power is magnified when combined with our other services.
We can bundle these services to create a holistic, defense-in-depth security strategy.
Learn more about endpoint security, threat detection, and protecting your devices.

Every device your business uses is a potential entry point for cyber threats. Endpoint Detection and Response (EDR) helps SMBs monitor, detect, and respond to these threats.

One of the best methods to protect your business from cyber attacks is by educating your employees about cybersecurity threats.
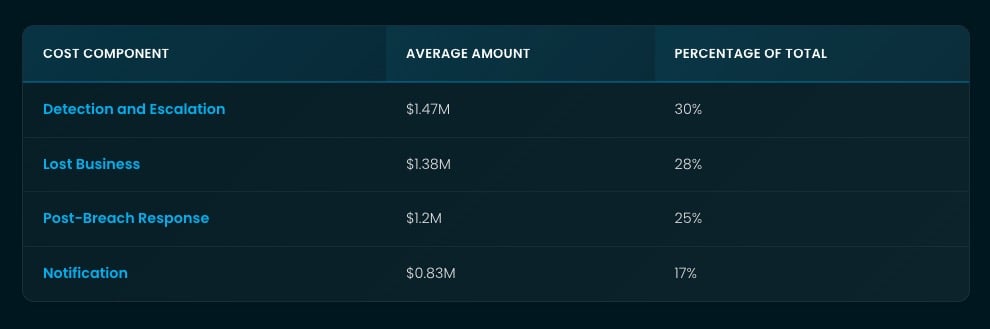
Average phishing attack costs for 2025 including direct losses, recovery expenses, downtime impact, and prevention strategies
Ready to see what's really happening on your endpoints and stop threats before they become breaches?
Contact Us