
What SMBs Need to Know About Endpoint Detection and Response (EDR)
Every device your business uses is a potential entry point for cyber threats. Endpoint Detection and Response (EDR) helps SMBs monitor, detect, and respond to these threats.
Total Assure offers a continuous, expert-led program to proactively discover, prioritize, and remediate the security gaps across your infrastructure before they can be exploited. We don't just hand you a list of problems; we provide an actionable roadmap to a stronger security posture. Total Assure's service provides:
Our Vulnerability Management service is not a one-time scan; it's a continuous lifecycle designed to systematically reduce your risk over time. We combine powerful technology with expert analysis to deliver a program that is both comprehensive and efficient.
Our methodology is a continuous, five-stage cycle:
We begin by creating a comprehensive inventory of every asset on your network, including servers, laptops, printers, and cloud instances. You can't protect what you don't know you have.
Our advanced scanning tools systematically probe these assets for tens of thousands of known vulnerabilities, misconfigurations, and missing patches.
A raw scan report can be overwhelming, listing thousands of low-risk issues. This is where our expertise becomes critical. We analyze the scan results, correlating them with threat intelligence and the business context of each asset to prioritize the vulnerabilities that pose a genuine risk to your organization.
We provide your IT team with clear, actionable reports that detail not just the vulnerability, but the exact steps needed to fix it. We track the entire remediation process, offering guidance and support along the way.
We conduct follow-up scans to verify that the vulnerabilities have been successfully remediated, providing measurable proof that your risk has been reduced. This entire process then repeats, ensuring continuous improvement of your security posture.
Bundled compliance and security: together with our partner, Tenable, we assess your attack surface, inventory network systems, and gather data from workstations, devices, and servers.
We utilize an industry-leading vulnerability scanning platform, consistently recognized for its accuracy and the breadth of its vulnerability database. Our technology includes authenticated network scanners, cloud connectors, and lightweight agents to ensure comprehensive coverage across your entire on-premise and cloud environment without disrupting your operations.
Our implementation is designed to deliver value quickly:
Our VM service translates technical vulnerability data into a strategic risk reduction program that delivers clear business benefits.
The return on investment (ROI) for Vulnerability Management is measured in the cost of avoided breaches and increased operational efficiency. By systematically eliminating attack vectors, you prevent costly incidents. Furthermore, by providing prioritized, clear guidance, you save countless hours of your IT team's time that would be spent researching and chasing down thousands of low-impact alerts.
Penetration testing is a valuable, point-in-time assessment. However, your environment changes daily. Vulnerability Management is the continuous process that happens between those tests, ensuring that new weaknesses are found and fixed as they emerge, providing constant vigilance.
No. Our modern scanning tools are designed to be non-intrusive. We schedule scans and use intelligent, resource-aware technology to ensure there is no disruption to your business operations.
Our service is designed specifically to make your team more efficient. By providing expert prioritization and clear remediation guidance, we eliminate the noise and research, allowing your team to focus only on fixing the vulnerabilities that matter most. We handle the heavy lifting of discovery and analysis.
A vulnerability is a weakness or a security hole in a system (like a missing patch). A threat is an actor or event (like a hacker or a piece of malware) that could exploit that weakness. Our VM service focuses on systematically eliminating the vulnerabilities, thus removing the opportunity for threats to succeed.
We use a risk-based model that goes beyond the standard CVSS score. We factor in real-time threat intelligence (is this vulnerability being actively exploited in the wild?), the asset's exposure (is it internet-facing?), and its business criticality to pinpoint the true risks to your organization.
Vulnerability Management is a critical proactive service that works hand-in-hand with our other security offerings.
We can bundle these services to create a comprehensive, defense-in-depth security strategy.
Learn more about vulnerability management, patch management, and proactive security.

Every device your business uses is a potential entry point for cyber threats. Endpoint Detection and Response (EDR) helps SMBs monitor, detect, and respond to these threats.

One of the best methods to protect your business from cyber attacks is by educating your employees about cybersecurity threats.
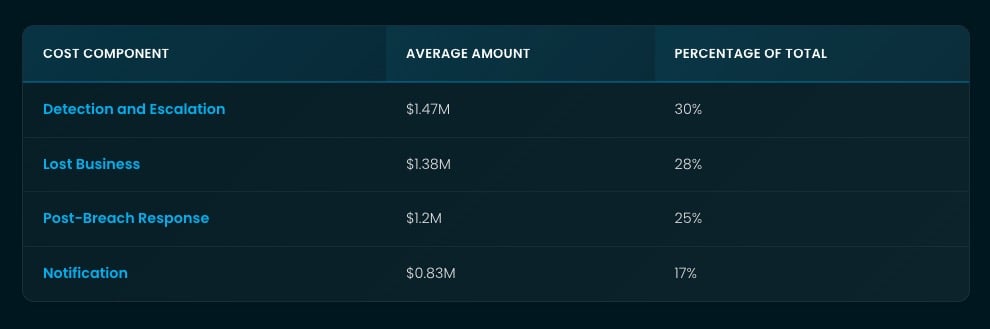
Average phishing attack costs for 2025 including direct losses, recovery expenses, downtime impact, and prevention strategies
Ready to move from a reactive to a proactive security posture and close the door on attackers?
Contact Us