What This Means for Your Organization:
- Zero Trust assumes all network users are potential threats.
- Zero Trust strengthens your organization’s security posture by modernizing your cyber security framework and by continuously monitoring potential threats.
- Using Zero Trust enables your business to reach compliance and security standards.
What Is Zero Trust?
Zero Trust is a framework built on the core principles of never trusting and always verifying. Previously, frameworks would assume users within their network were trustworthy, but this has evolved over time to trust no one inside or outside of the organization. Zero Trust assumes that every user, device, or system, inside or outside your network, can’t be trusted without continuous verification. The Zero Trust framework is always monitoring the network to make sure access requests receive proper verification and authentication. Continuous monitoring is a crucial component of Zero Trust along with Multi-Factor Authentication (MFA) authentication like Google or Microsoft Authenticator, role-based access, and conditional access policies.
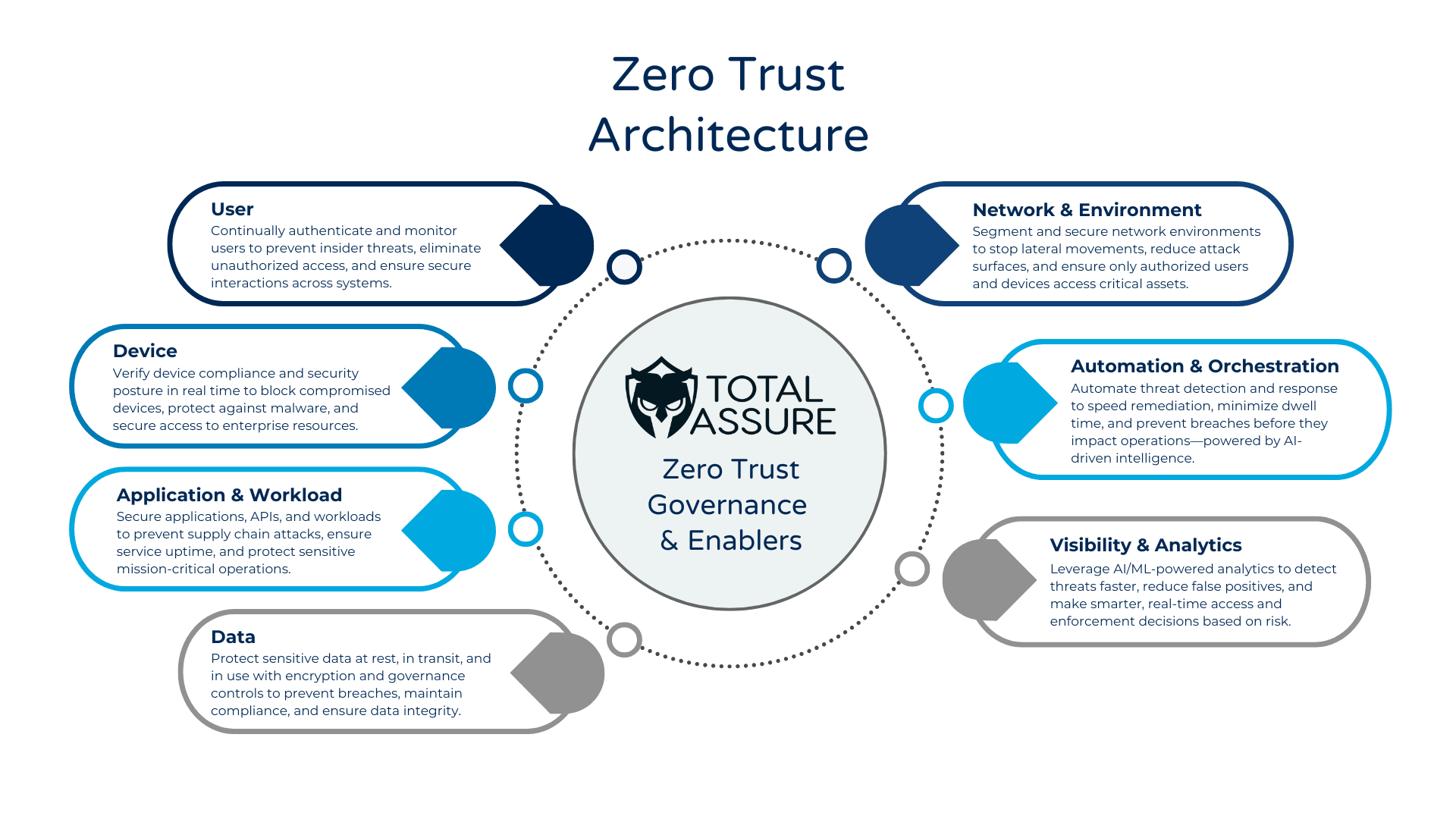
Why Is Zero Trust Important?
Having a Zero Trust framework in place will secure your business against modern cyber attacks. The U.S. government has also underlined the importance of Zero Trust in Executive Orders and mandated the use of Zero Trust for federal government agencies. With the key points highlighted by CISA and the Zero Trust Maturity Model, you can better understand the core of Zero Trust and its usefulness. Not only is Zero Trust a crucial component of modern network security, it also allows for companies to meet specific compliance requirements for other frameworks such as the NIST SP 800-171 and CMMC certifications.
What You Can Do Now
- Evaluate your current architecture through the lens of Zero Trust. Do you know who’s accessing what, when, and how?
- Map your tools and processes against NIST 800-207 and CISA’s maturity model.
- Prioritize identity, access management, and continuous monitoring. These are some of the foundational pillars of any Zero Trust approach.
- Avoid “Zero Trust-in-a-box” solutions. Instead, build an adaptable strategy that reflects your mission and your risks.
- Don’t wait for an audit or mandate to begin. Zero Trust by default means readiness is not just encouraged, it’s expected.
Total Assure: Your Partner in Zero Trust
Our team at Total Assure specializes in helping small- to medium-sized businesses operationalize Zero Trust. From compliance alignment to cloud migration, we deliver tailored, cost-effective architectures that meet today’s compliance requirements and tomorrow’s challenges.
About Total Assure
Total Assure, a spin-off from IBSS, provides uninterrupted business operations with our dedicated 24/7/365 in-house SOC, robust managed security solutions, and expert consulting services. Total Assure provides cost-efficient, comprehensive, and scalable cybersecurity solutions that leverage 30 years of experience and expertise from IBSS. Total Assure partners with its customers to identify security gaps, develop attainable cybersecurity objectives, and deliver comprehensive cybersecurity solutions that protect their businesses from modern cybersecurity threats.
For more information on how Total Assure can assist your organization, book a free 30-minute consultation.











